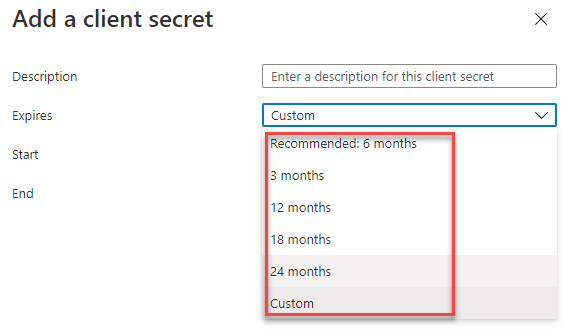
App secret valid longer than 24 months
As you might know, it’s only possible to create app registrations secrets that are valid for a maximum of 24 months. At least in the Azure UI. The process of creating it in the UI I described in an earlier post. In this blog post, you will learn how to create an app secret valid longer than 24 months.
In the section “Summary” you can find everything you’ll need in case you don’t need all the explanations.
Problem
In general, I think it is a good idea to change a secret regularly. The Problem with the Power Platform is that we have to do a bunch of manual stuff whenever the secret expires. For example, every connection reference using the App registration needs to be reconnected manually.
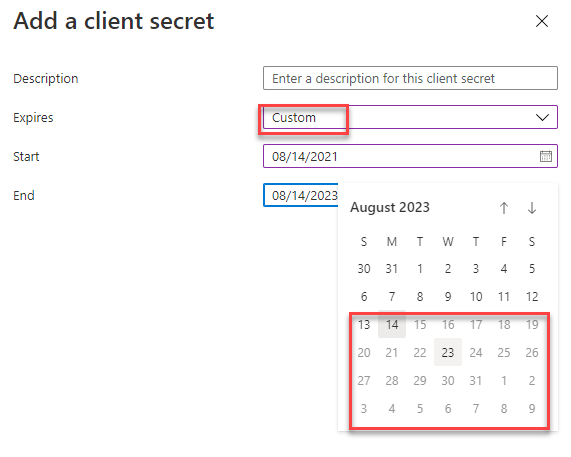
Which means when you use a App registration with parts of the Power Platform you normally want the secret to be valid longer than 24 months. As mentioned this is not possible to achieve in the Azure portal as seen on the following screenshots.
Solution
The solution is to create the secret via a console. With that, one could create secrets that last as long as you’d need.
There are two different ways of doing it I know of.
- Via the Azure CLI prompt in the Azure portal. As described on Tip #1404 of CRM Tip of the Day
- Via a Azure cmdlet called New-AzureADApplicationPasswordCredentials
In this post, we will take a look at the second approach.
All the credit for this should go to Isaac Stephens (LinkedIn & Twitter) for coming up with the solution. As well as Gayan Perera (LinkedIn) for letting me know.
Implementation/Configuration
So let’s get to work and implement/configure our solution.
Install AzureAD Module
First of all, we have to install the AzureAD PowerShell module.
To do so we open an Admin elevated PowerShell and type the following command.
Install-Module AzureAD
Define Dates
The next step is to define the start and end date in between the secret should be valid.
First, we save today’s date in a variable called “startDate”.
$startDate = Get-Date
We then add X years to it and save it as the end date. In our case, we add 10 years.
$endDate = $startDate.AddYears(10)
Connect to Azure
To be able to execute the command we would like to run we have to connect the current session to Azure. We use the following command for that.
Connect-AzureAD -Confirm
This will open a popup where you can sign in with the correct credentials.
Create secret
Now we come to the real part of this solution.
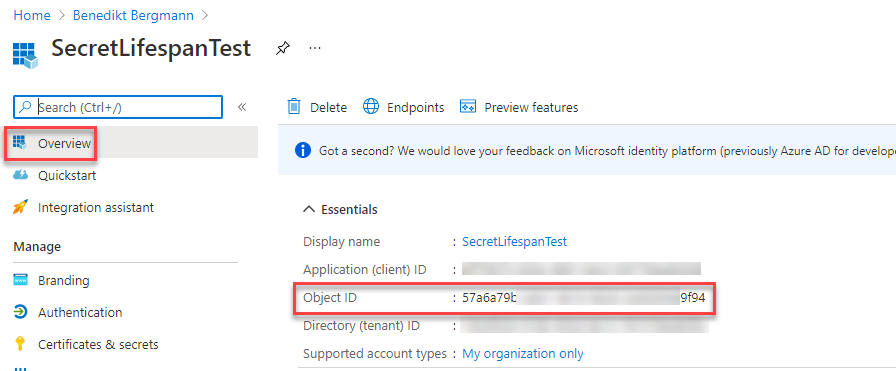
For the following command we need the start and enddate, a custom identifier which could be whatever you’d like as well as the ObjectId of the App registration in question. This you can find in the Azure Portal in the overview of the App registration.
The command runs the mentioned cmdlet to create a new secret which starts at our defined startdate and ends at the enddate. The result is saved in a variable called “aadappsecret”.
$aadappsecret = New-AzureADApplicationPasswordCredential -ObjectId <ObjectID> -CustomKeyIdentifier "MySecret" -StartDate $startDate -EndDate $enddate
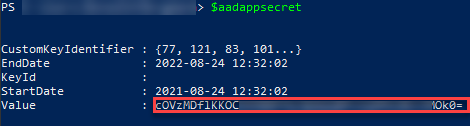
If you write the variable name in the powershell it will print it out. In the result of that you will find the value of the secret which you need to save for later use. Here is the command for that
$aadappsecret
In my case it looked as followed.
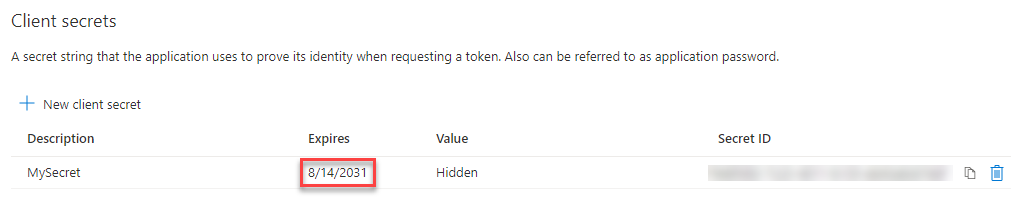
If I take a look in the Azure portal it looks like this.
Now you have a secret which lasts longer than 24 months (in our case 10 years).
Conclusion
As described there are several solutions to create an App secret valid longer than 24 months. If you know how to do it it’s not very complex to achieve a longer valid secret.
I hope this post helped you. Feel free to contact me if you have any questions.
Summary
You need the object ID and execute the following commands.
To install the module you might need an elevated PowerShell.
Install-Module AzureAD $startDate = Get-Date $endDate = $startDate.AddYears(10) Connect-AzureAD -Confirm $aadappsecret = New-AzureADApplicationPasswordCredential -ObjectId <ObjectID> -CustomKeyIdentifier "MySecret" -StartDate $startDate -EndDate $enddate $aadappsecret
You can also subscribe and get new blog posts emailed to you directly.
I was reading about this a few days ago seeing as they closed off the UI way of having non-expiring secrets, I think, for some time now.
It seems like MS have some plans to limit the lifetimes of these secrets administratively but no timelines or etas, but, reading between the lines, I can only assume they’ll be gradually closing off all these avenues of being able to set non expiring secrets.
What I don’t understand is why they don’t provide some dashboard in azure where one can see secrets coming up for expiry or easily query when they all expire, Imagine those orgs with potentially hundreds of apps functions using these app registrations, and overnight the secret expires…
I do agree. Such a Dashboard would be nice. More importantly, would be good tooling to change a secret for everything like connections in Power Automate.